
When hunting for signals of interest, there is one critical question: does your mission need to be achieved in real time or via post processing?
If your application is not time-sensitive, you can utilize I/Q recording solutions that record “everything” across a wide frequency range in high fidelity. Sure, these systems generate enormous data sets, but you have the time and tools to perform such analysis at your convenience. But the reality in tactical and field deployments is not as comfortable.
The reality in tactical and field deployments
Many field missions are extremely time sensitive. Failure to detect specific signals of interest could be a serious tactical disadvantage, impact mission success, or worse, a threat to material and life. From triggering when specific red team emissions are on air, jamming, drone signals, or targeting Radar, many applications require real-time action based on real-time spectrum monitoring data.
If your application is time sensitive, the ability to accurately detect specific signals of interest in real time should be of enormous interest. How do you filter from the thousands of signals, instantaneously exploiting the spectrum to detect and operate capture and geolocation workflows against a specific signal of interest?
Two key triggering methods are available: traditional mask-based triggering or the use of real-time signal detectors operating in the software domain.
This blog compares and examines the benefits of each technique.
How to decide if you have time or want to sweep in real time?
Some spectrum managers have a good idea of where they will find signals of interest: spectrum managers working in signals intelligence, organizations such as NSA and GCHQ, and even some front-line soldiers recording I/Q for specific bands who then analyze the data to look for frequency hopping, enemy communications systems, Radar, etc.
In this instance, the best process may be to capture and store all signals within a frequency range of 100 MHz using long duration, wideband RF Recorder (such as the RFeye SenS Portable or RFeye SenS Remote) that creates high-fidelity I/Q data.
By recording the whole signal over a long period, it is possible to capture, replay, find, isolate, and analyze the signal and then build a pattern of life. Once the data has been recorded, the challenge is identifying and analyzing signals of interest using forensic signals analysis software. If necessary, the signals can then be passed on for classification, decoding, and decryption work.

Figure 1: Workflow when recording wide bandwidth I/Q data
However, other spectrum managers may be interested in usage patterns, signal characteristics, and interference sources. Gathering this data in real time helps to make informed decisions regarding frequency band allocations, identifying potential sources of interference, and optimizing the overall use of the available spectrum.
This application involves sweeping multiple frequency bands and setting triggers for when signals of interest appear on air. When a signal of interest is identified, the spectrum manager will likely want to capture, classify, and geolocate the signal before potentially decoding it.
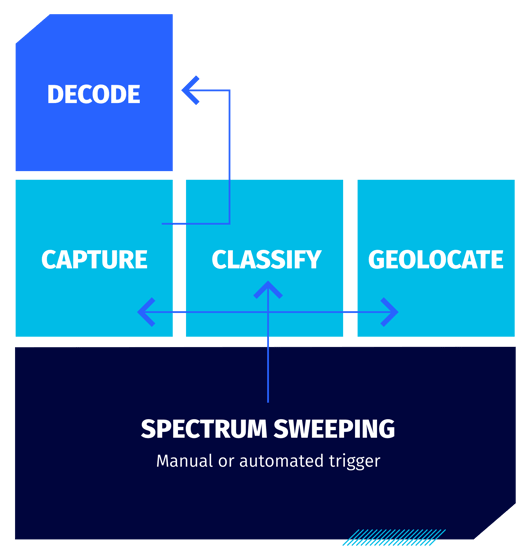
Figure 2: Workflow when spectrum sweeping in real time
Traditionally, spectrum masks have been used as triggers in such workflows. While this is acceptable for specific applications, there are many scenarios in which false detections can be made (desensitizing the operator) or important signals can be missed. Software detectors are a far more efficient and precise method of detecting signals of interest and driving the important capturing, classifying, and geolocating workflows.
What is a mask-based trigger system?
A mask is a line of fixed amplitude superimposed on the live spectrum; if the live spectrum breaks the mask, there is a trigger. In a congested spectrum band, it is possible to set an appropriate mask to accommodate known signals and only trigger on signals of interest.
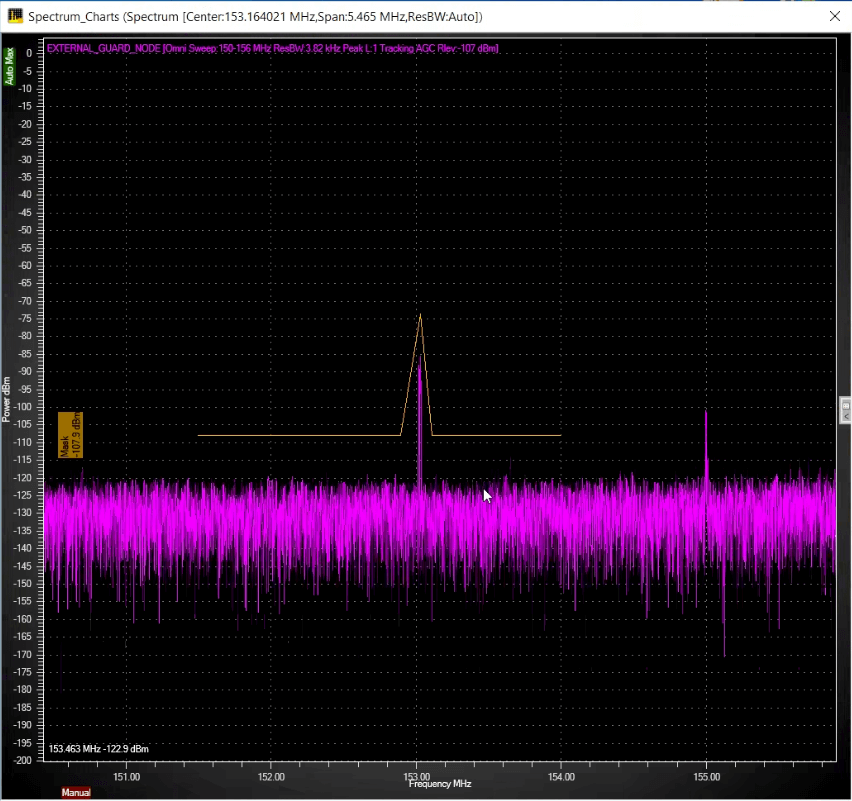
Figure 3: A simple mask (blue line) on the spectrum is triggered by any other signal penetrating it.
However, if operators employ this process, they can build complex masks which can efficiently focus their targeted analysis on signals that meet specific criteria by employing a mask-based trigger during RF signal analysis. The mask function includes starting with straight lines, “learning” from existing spectrum, or manually adding passbands for known signals. Traditionally, this system has been used to help streamline the analysis process and enhance the ability to focus attention and gain meaningful insights from complex spectrum data.
Enhancing mask break data with frequency allocation data
When analyzing the spectrum, an operator will significantly benefit from augmenting the view with an overlaid frequency allocation table (FAT) on the spectrum. Then, when utilizing traditional mask break triggering, they can add important data on the detected signal of interest.
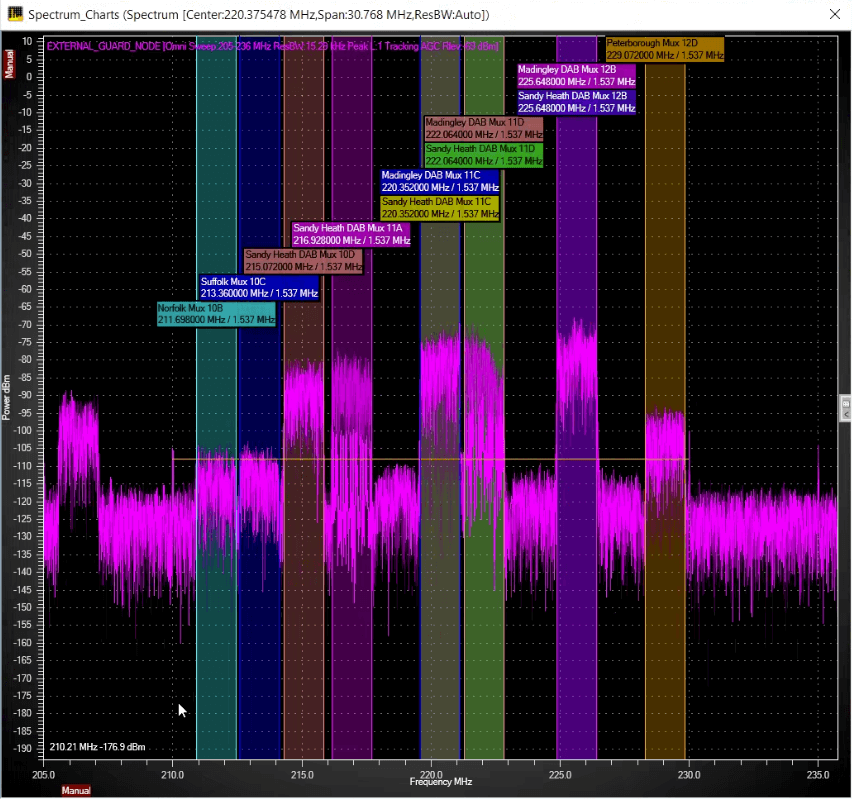
Figure 4: Mask set at -100 with many DAB channels breaking through.
Whenever the mask is broken (and triggered), spectrum monitoring software creates an intercept table that records crucial information:
- The time and date of the signal of interest
- The RF Receiver (Node) that captured the signal
- Counts
- The frequency of the signal
- The bandwidth of the signal
- Occupancy level
- Minimum and maximum power
- Is the signal stored on the user’s previously compiled database?
Using a mask as a trigger together with an intercept table is a powerful combination as the operator can see if the signal of interest is on the frequency allocation table. Any unrecognized signal could potentially indicate a problem.
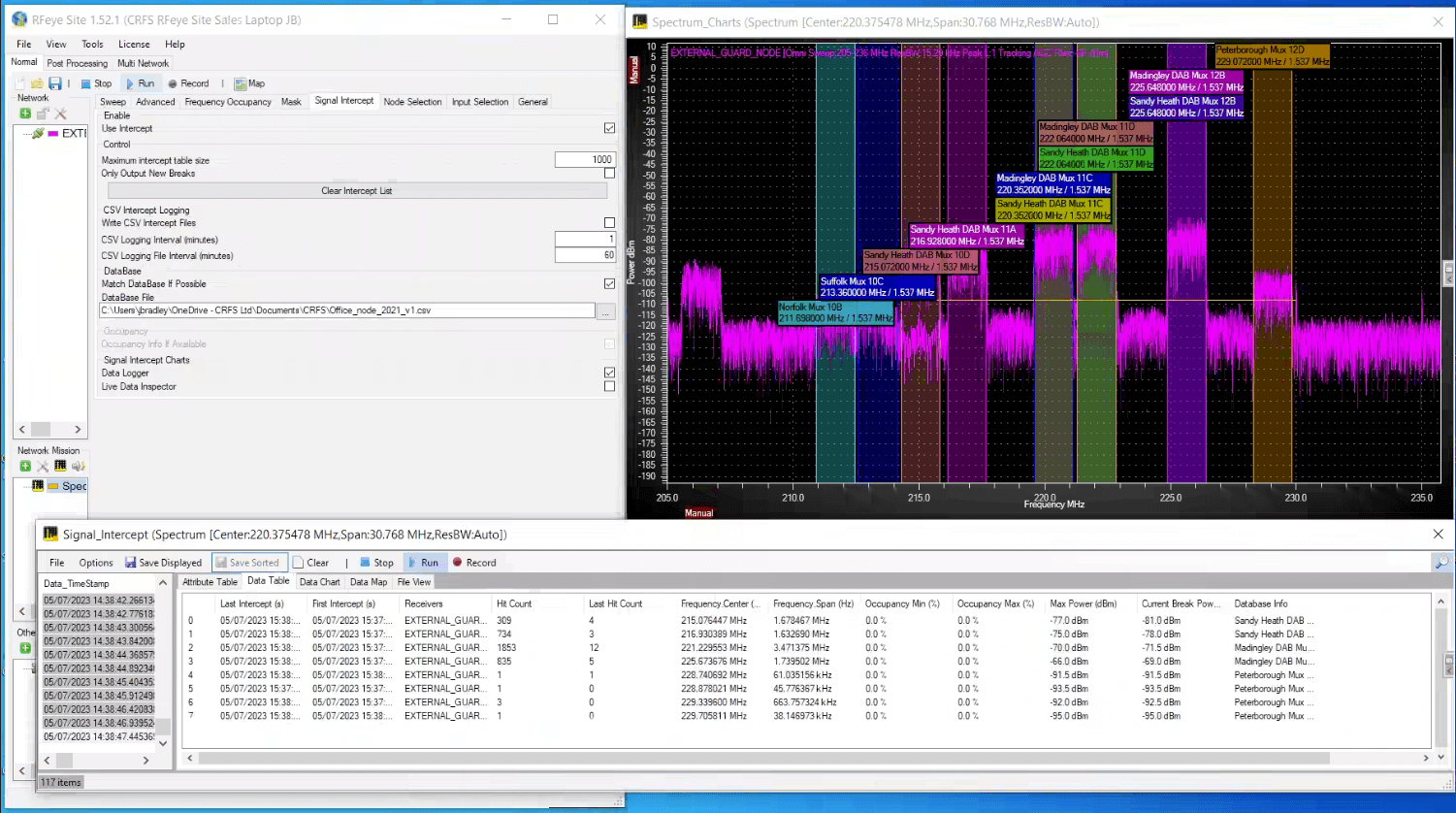
Figure 5: Software showing a mask trigger and an intercept table
Automated software can be set to raise alarms and incidents when specific masks are broken or send email notifications to selected users. Moreover, the software can also instruct specific RF Receivers to complete a triggered task—capturing I/Q data, classifying the signal of interest, or geolocating the signal of interest.
Pros and cons of mask-based triggering
When there is low signal occupancy and a very low noise floor, masks are exceptionally useful as this allows the spectrum analyzer to focus on a very low number of signals of interest that come on air.
In non-congested and flat areas of the spectrum, such as the GPS band at 1.6 GHz, masks can be very effective. For example, a mask would easily detect a jammer, which protrudes abruptly from the spectrum.
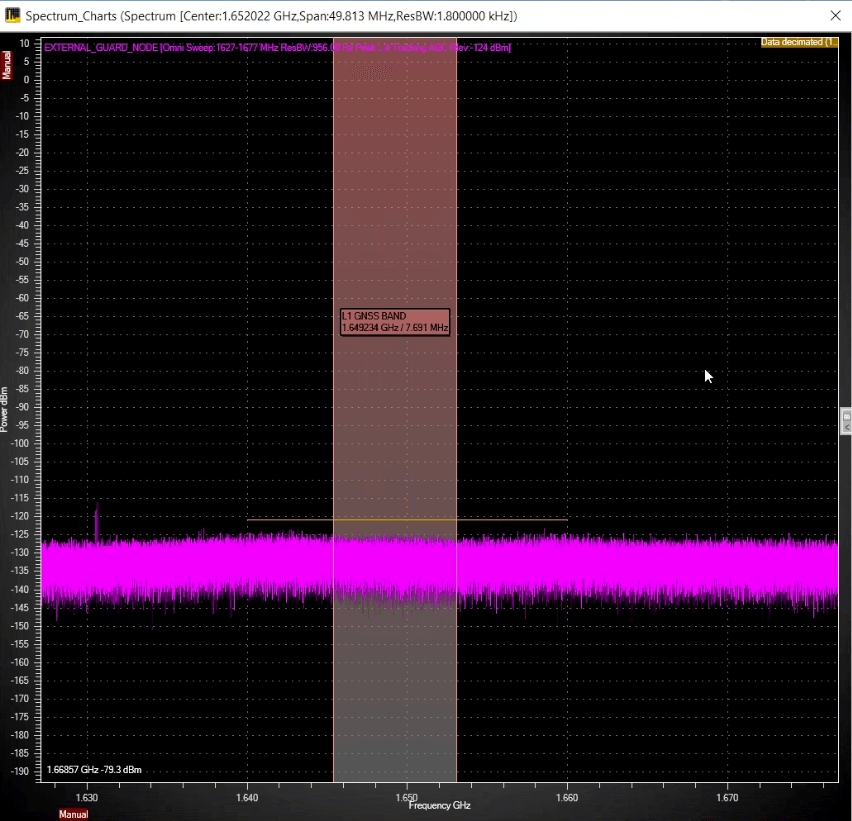
Figure 6: GPS band
However, masks can be problematic in a frequency band with high occupancy, congestion, or with a high noise floor—a simple example is to observe for a few moments the 2.4 GHz ISM band and see the extreme congestion that the Internet of Things brings as various devices are all using Wi-Fi, Bluetooth, etc. for signaling.
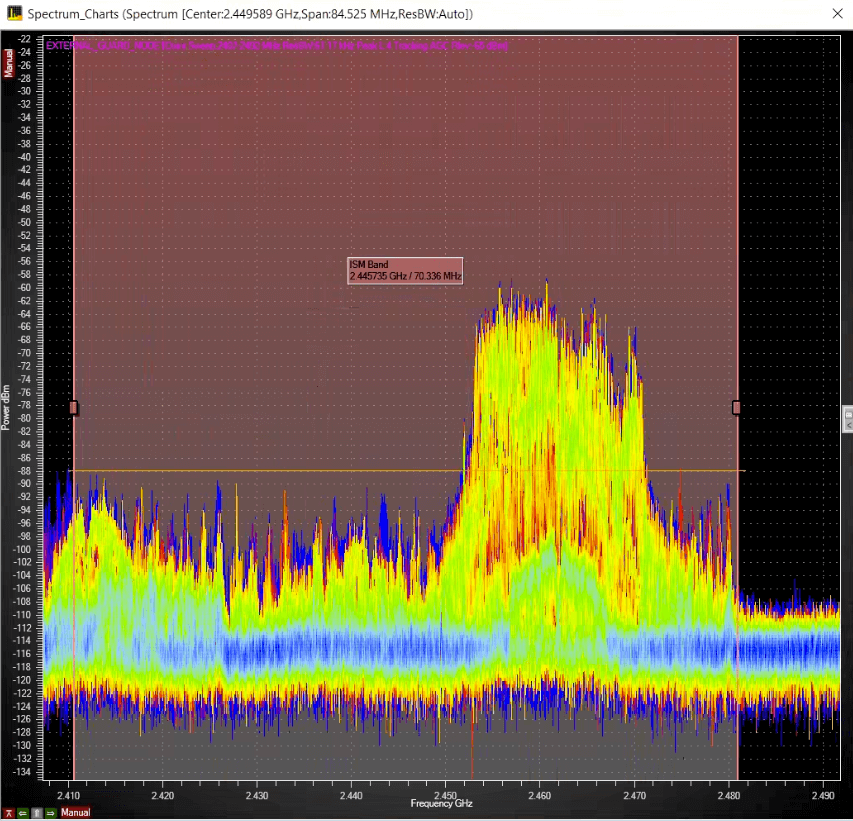
Figure 7: Example of spectrum with a high noise floor
In this case, setting a mask will hinder spectrum operators as many signals can break the mask and set off triggers. As there is no way to discriminate between different signals of interest, there will be many false positives, and many signals of interest will be missed. Also, as masks can only look for one signal at a time, they trigger the highest signal at any one moment—but there is no way of guaranteeing that the highest signal is the signal of interest.
Furthermore, if a signal of interest travels over a long distance, it will be very close to the noise floor; therefore, the mask can be triggered by noise as well as the signal of interest. Therefore, there is a limit to how close to the noise floor it is possible to set the mask.
In a congested spectrum, masks do not allow the spectrum analyzer to discriminate between signals—they cannot identify signals of interest or run the subsequent capture, classify, and geolocate workflow.
To discriminate against spurious noise or signals that are not of interest, CRFS pioneered signal detectors operating in the software domain.
What is a signal detector?
If a signal is a fingerprint, the signal detector is a fingerprint scanner—they characterize thousands of signals' frequency, power, and time characteristics in real time, analyze, compare, and, if appropriate, act. As the receiver (RFeye Node) is sweeping, the signal detector is tirelessly analyzing, comparing each signal it detects to its library of stored signals to check for matches.
It only triggers when the signal of interest matches a pre-stored signal’s frequency, power, and time characteristics. In effect, detectors are signal discriminators on a massive scale. They can also work very close to the noise floor, eliminating one of the key weaknesses in mask-based systems and offering a much wider operational range.
As signal detectors operate on the RF receiver, spectrum managers benefit from more range and coverage but still benefit from a very low backhaul requirement for a true edge-processing capability. All data is processed and analyzed on or near the receiver rather than being sent to a centralized cloud. With such edge computing, data is processed and analyzed at or near the edge device, reducing latency, network bandwidth requirements, and dependence on a centralized cloud infrastructure. This enables real-time or near-real-time decision-making and faster response times.
How do signal detectors work?
Signal detectors are an algorithm that takes in thousands of signals in real time, determines each signal's key time and frequency characteristics, then compares them to a preset series of parameters that the user can define based on their mission.
This library of parameter types can either be a very highly defined pre-determined series of settings or some generic signal family settings. The most precise detection work is highly deterministic, and with prior knowledge of the signal, one can perform extremely precise filtering and identification.
There are two types of detectors: pre-build detectors for some common signal types and generic detectors that the user can “fine tune” to any signal of interest across the receiver operating range.
Out-of-the-box detectors have very specific time and frequency characteristics and are written for particular signals, including ADS-B/IFF/TACAN/Link16 for aviation or AIS in maritime.
However, if a particular signal of interest’s characteristics are unknown, its time and frequency characteristics can still be captured and measured. It is possible to write detectors with a massive range of time and frequency characteristics to match any signal—which can then be added to the library of detectors built for any signal anywhere on the spectrum.
The detector can be programmed to search a specific or a wide frequency band—only triggering a workflow if they detect the signal of interest. This is particularly useful when faced with adversaries who practice non-standard spectrum utilization or frequency hopping techniques.
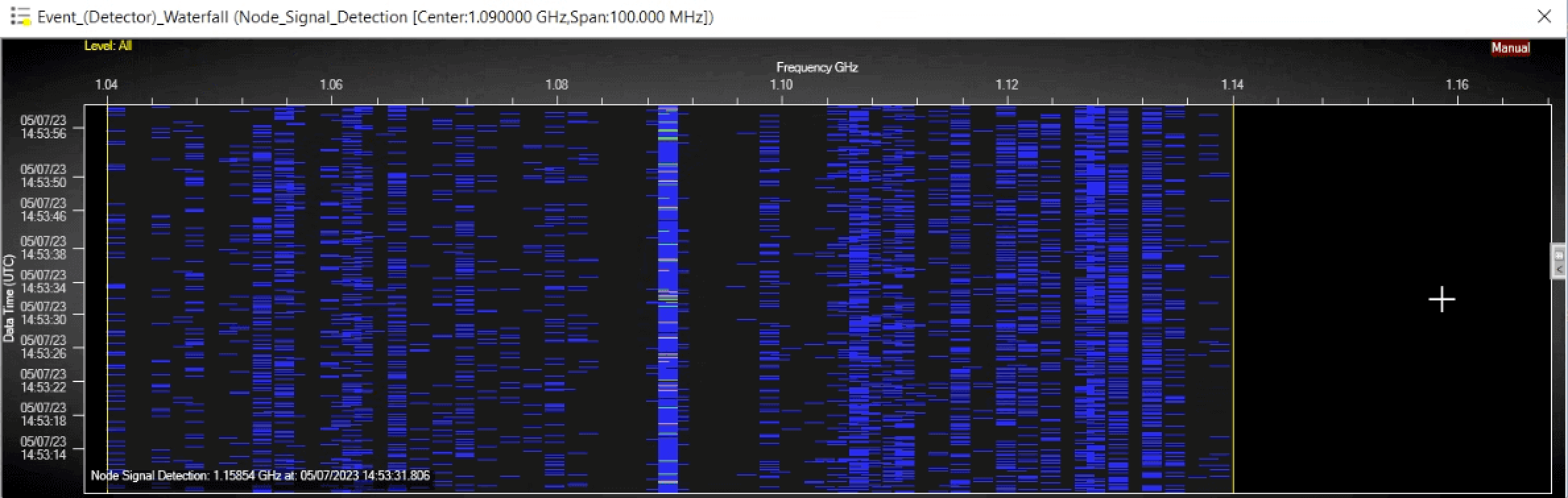
Figure 8: Detectors firing.
Signal detectors in action
To demonstrate the power and capability that signal detectors provide, let's conclude with an example from the very first application for which they were developed.
Signal detectors were first designed as part of CRFS’ capability to detect and perform 3D tracking of airborne assets passively. For civilian aircraft, two common RF transponders are Automatic Dependent Surveillance–Broadcast (ADS-B) and Tactical Air Navigation System (TACAN) signals. If you observe the spectrum in real time, these signals pulse rapidly, are extremely low to the noise floor, and (in the case of TACAN) are frequency agile. No human operator could hope to consistently perform detection and geolocation tasks against such a complex and uncooperative scenario.
To achieve what humans could not, the CRFS solution was to automate the detection of signals of interest using signal detection, then trigger the 3D geolocation and tracking workflow with highly precise triggering data.
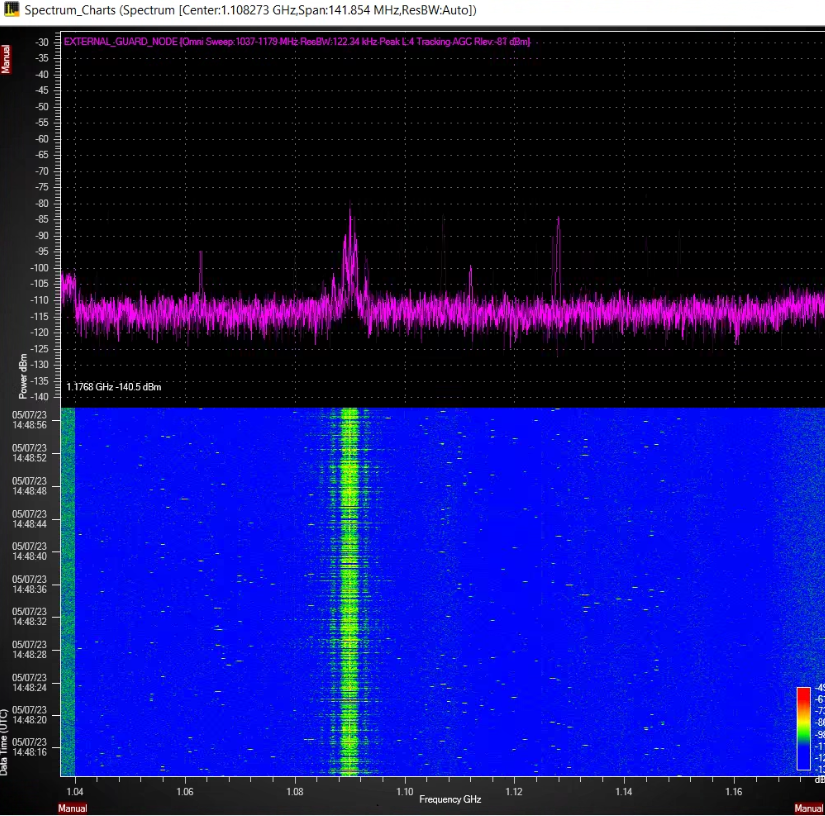
Figure 9: An ADS-B pulse from an airplane at 1090 MHz (clearly seen in the middle). However, the waterfall also shows TACAN signals at different channels and frequencies, which would be impossible to see without the detector.
Conclusion
Mask-based triggering is the traditional and well-known method of triggering from live spectrum for specific signals of interest. The technique is useful when the spectrum is not crowded and when there is a very low noise floor. However, with the increased congestion and complexity faced in the electromagnetic spectrum, even an experienced operator could struggle to discriminate and focus on those specific signals of interest that are mission-critical to them.
CRFS signal detectors can be levered to discriminate specific signals in real time, regardless of how congested the spectrum may be. With such specificity, automated workflows that capture, classify, and geolocates signal can operate in real time and with very low false positives.
Web page
Real-time spectrum monitoring & geolocation toolkit
CRFS' RFeye Site software provides all the essential functionality needed for full spectrum operations, turning spectrum data into RF intelligence.
Jon Bradley
With over 6 years of experience, Dr Bradley enjoys close collaboration with a range of CRFS clients to help them understand how to lever CRFS technology and what advantages the RFeye ecosystem can bring in real-world scenarios. Leading our Rest of World commercial team, he brings over 30 years of experience and know-how in both theory and in practice. When not living, sleeping, and dreaming about science, he enjoys hiking with Hugo the RF retriever who often appears in his posts.

