How to address GPS jamming in high-jamming environments
Modern navigation is as dependent on an accurate GNSS feed as Columbus was on his compass. The eastern Mediterranean, Black Sea, areas of the Baltic, Poland, and parts of Scandinavia are heavily jammed areas—which has negatively impacted the safety of maritime and air navigation, both military and civilian.
Jump to
Overview of GNSS and GPS
How does GPS jamming work?
High GPS jamming areas
Electronic protection techniques for GPS jamming
Assessing the probability of jamming
Geolocating the source of the jamming
Conclusion
Ceasing operations is not an option, and moving around the jamming is costly, so operators must rely on technology that allows electronic protection, jamming identification, and geolocating the source of the jamming.
Overview of GNSS and GPS
GPS is just one (albeit the most popular) GNSS satellite constellation and navigation system. The other constellations are the EU’s Galileo, Russia’s GLONASS, China’s Beidou, Japan’s QZSS, and India’s IRNSS.
GPS uses satellites, each sending signals to a GPS receiver on Earth. This transmits a high-resolution timing signal, from which the GPS receiver can compute the exact coordinates through triangulation, using at least four or more different satellite signals to compute its location.
GPS uses the following frequency bands:
- L1 Band (1575.42 MHz): mainly non-military use
- L2 Band (1227.60 MHz): mainly military use
- L5 Band (1176.45 MHz): A newer band designed for more demanding applications, offering improved resistance to interference and better signal strength
When they reach Earth, satellite signals are weak (less than 50 watts) as they must travel over long distances, making them vulnerable to jamming.
How does GPS jamming work?
Jamming is attributed interference, using which adversaries intentionally deny comms. GPS signals are susceptible to jamming because they are very weak by the time they reach the GPS device.
GPS jammers work by interrupting the signals from GPS satellites, making it difficult for a GPS receiver device to operate. An oscillator generates an RF signal at the frequency used by GPS devices. This signal is amplified to a strength sufficient to overpower or jam GPS signals within a certain range, with the amplifier’s adjustability allowing for flexibility in the jammer’s operational scope.
The amplified signal is transmitted through an antenna, which broadcasts the interference, affecting GPS signals. This reduces the signal-to-noise ratio at the receiver, making it difficult or impossible for the GPS receiver to discern the actual GPS signals from the background noise. Overseeing these components, the control circuit adjusts the oscillator’s frequency and the amplifier’s power, fine-tuning the jammer to specific requirements.
Types of GPS jamming
There are two types of jamming: blocking and spoofing. The first two methods below are examples of blocking, while the third is an example of spoofing.
Continuous Wave (CW) jamming: In this simple yet effective method, a jammer continuously emits a single frequency or a narrow band of frequencies. This makes it difficult for receivers to process incoming signals as they are flooded with a steady stream of unmodulated signals.
Narrowband jamming: A jammer emits signals at specific, narrow frequency ranges (2 MHz), directly targeting the GPS frequency. This method allows for precise targeting of enemy frequencies while minimizing disruption to adjacent bands, avoiding disruption to friendly signals.
Modulation techniques: There are several modulation techniques to jam GPS. Conversely to the above techniques, which are noise-based, meaning they overwhelm GPS, modulation techniques involve the transmission of signals that are similar to genuine GPS signals. They make it complex for GPS to determine between true and false information. Modulation techniques involve spoofing, which tries to deceive a GPS instrument by providing false location, and complex interference, which makes it difficult for GPS receivers to lock onto the correct satellite signal.
High GPS jamming areas
GPS jamming has become more prevalent since 2016. In the late 2010s vast areas were affected in South Korea, the Suez Canal, Cyprus, and Israel. In 2024, the eastern Mediterranean, Black Sea, areas of the Baltic, Poland, and parts of Scandinavia are the world’s most heavily jammed areas.
The image below shows levels of GPS interference during March 2024. High interference is shown in red, medium in yellow, and low in green. There is no data for the other areas. The image was taken from the open-source website GPSjam, which uses ADS-B signals sent by aircraft to estimate the severity of interference in the areas in which they are flying.
Image 1: Map showing global jamming hotspots 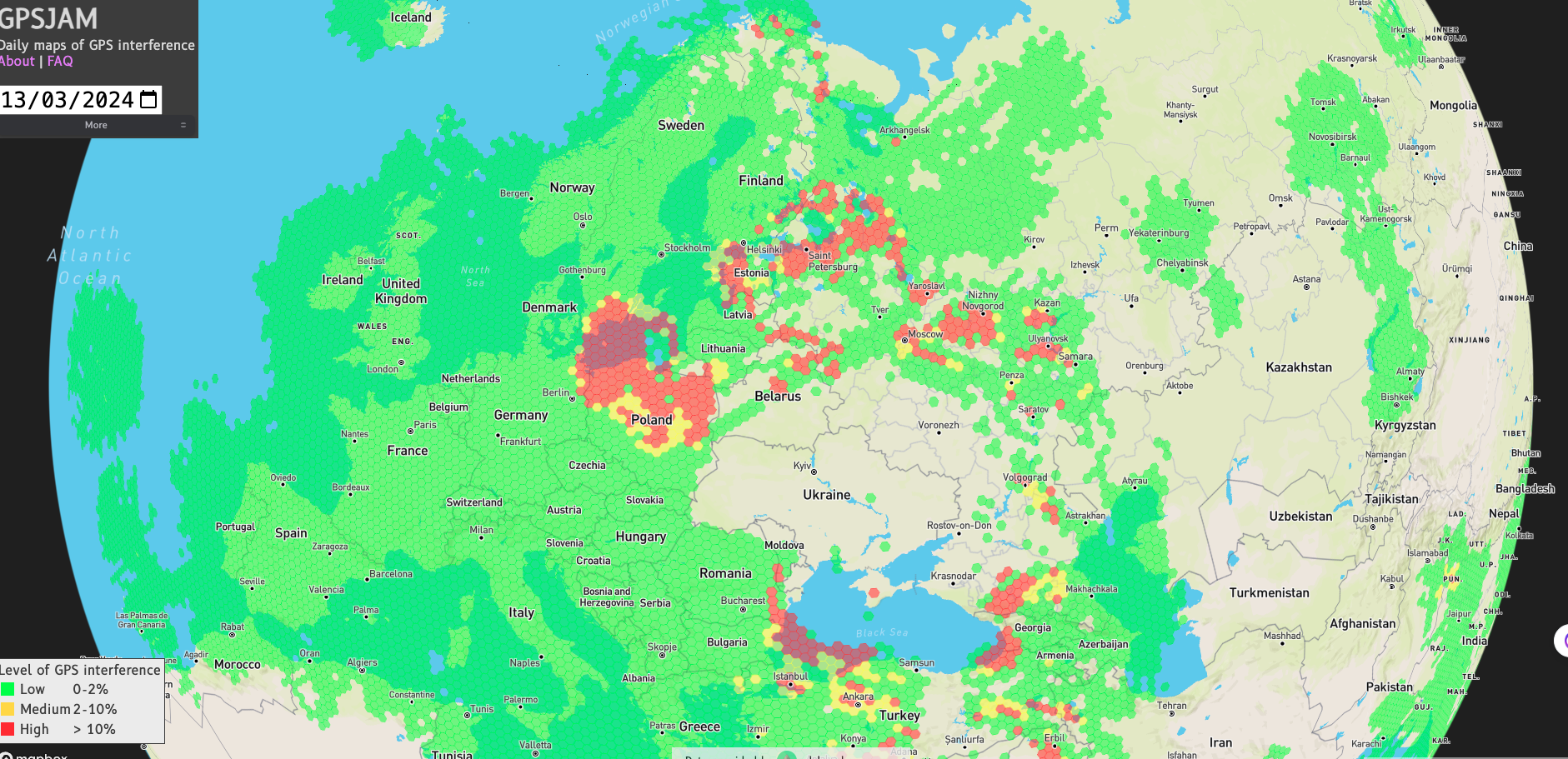
Source: https://gpsjam.org/?lat=44.17986&lon=44.89385&z=2.8&date=2024-03-13
GPSjam has charted the increase in GPS disruption, alerting insurers, agencies, and governments of the potential impact on shipping, aviation, and critical infrastructure.
Navigation is now achieved by GPS alternatives: ship captains are relying on traditional methods, pilots are switching to inertial reference systems, and the military is investing in multiple Assured Positioning, Navigation, and Timing (A-PNT) solutions.
However, despite GPSjam’s utility highlighting the issues in the public domain, it does not help GPS jamming victims, which include:
- Military forces (specifically those without assured PNT, like logistics, medical, airfields, and communications systems)
- Unmanned systems operators (UAV, USV, UGV)
- Ships and aircraft operating in and around these areas
- Critical civilian ports or airports near GPS jamming areas
Instead of simply avoiding these GPS jamming areas, victims can take proactive measures, including:
- Installing electronic protection techniques for GPS jamming
- Conducting pre-mission intelligence or risk assessment of jamming to signal ratios
- Geolocating the GPS jammer itself and sending the location to a military or police force
Electronic protection techniques for GPS jamming
One effective way to counter GPS jamming is to use Controlled Reception Pattern Antennas (CRPA) instead of standard GNSS antennas. CRPA are phased array antennas that shape their signal reception beams—minimizing the impact of jamming signals while optimizing the reception of GPS satellite signals.
For spectrum monitoring and geolocation tasks, CRFS can supply and fix CRPA to RFeye Nodes—to minimize the risk of GPS jamming.
Image 2: CRPA antenna connected to a CRFS RFeye Node 100-18
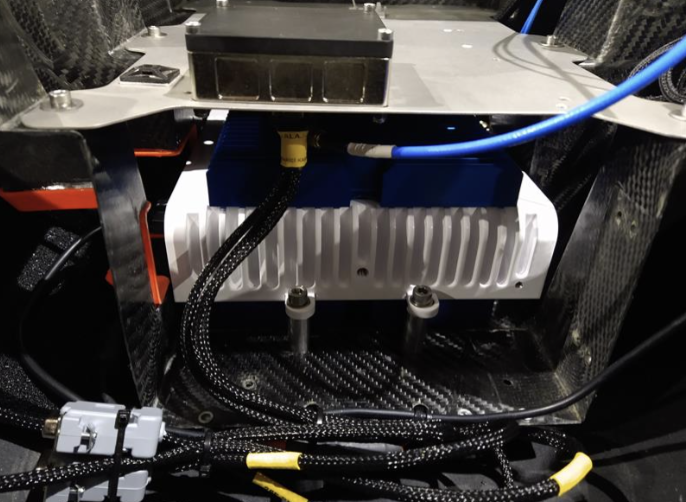
When the CRPA antennas detect GPS interference, they angle the beams toward the satellites while ignoring the GPS jamming signals.
CRPA antennas use the following techniques to optimize GPS performance.
Adaptive beamforming
The antenna pattern is dynamically adjusted towards the GPS satellites and away from sources of interference. The antenna array steers the beam, which enhances GPS signals while generating zones of minimal sensitivity elsewhere. By doing so, beamforming improves the signal-to-noise ratio of GPS reception, enabling more robust and reliable GPS performance, even in high-jamming environments.
Antenna gain
By increasing the gain of an antenna and simultaneously reducing the gain for signals coming from other angles, a receiver can more effectively receive signals from satellites while reducing signals from other directions. This approach relies on directional antennas that ensure the receiver locks onto and maintains a stronger connection with legitimate signals, improving GPS functionality.
Null steering
The array antenna array is manipulated to form an area where there is significantly reduced signal reception (a null). This is achieved by creating constructive interference (in the GPS satellite’s direction, which helps the wanted GPS signals), while also creating destructive interference (in the direction of the jamming, which nulls the interference.
Assessing the probability of jamming
There is no rapid way to determine if jamming is occurring; attribution requires detection and fusing that data with other intelligence. However, before other intelligence capabilities (such as overhead ELINT, IMINT, or COMINT) are applied, detection of the jammer inside the spectrum is usually the first step in this process.
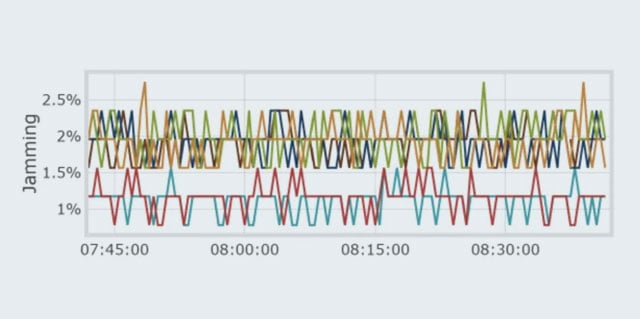
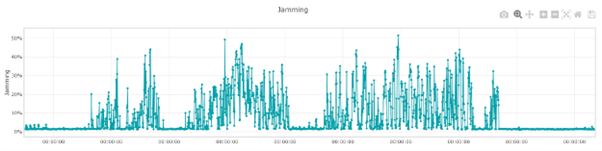
RFeye Nodes contain a jamming indicator provided by the u-blox chipset, which outputs a value from 0 to 256. CRFS automated spectrum management software, RFeye Mission Manager, has a feature that converts the number to a percentage, which is visually represented on a chart (as a percentage of jamming probability over time).
Image 3: Chart showing jamming as a percentage of jamming probability over time
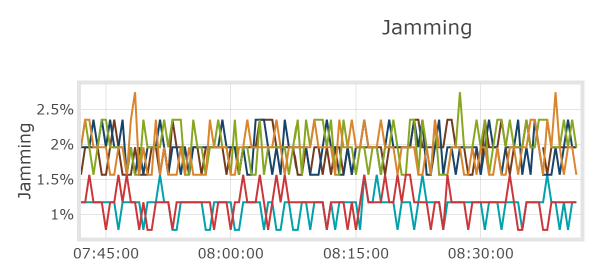
This feature is helpful as jamming is not always binary. A 30% jamming level could indicate several other possibilities in addition to intentional jamming by an adversary, including unintentional interference, the result of signal blockages, or a receiver fault.
By assessing the level of jamming over time, operators can keep a record of the jamming of a particular unit. During critical missions, operators are likely to want to monitor this feature continuously, so when the percentage passes a certain threshold, they can be alerted to carry out geolocations of the sources of the jamming.
Image 4: Probability of jamming in RFeye Mission Manager
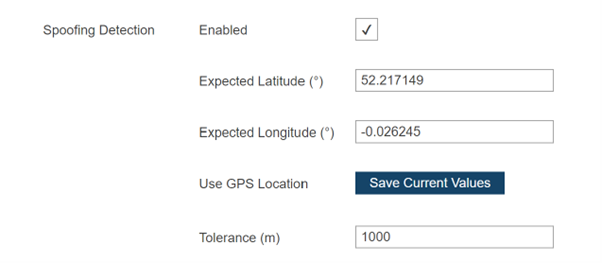
Spoofing detection
RFeye Nodes can also detect suspected spoofing.
Image 5: Spoofing detection alarm visible on the Node web page
Geolocating the source of the jamming
Once a percentage threshold of jamming has been surpassed, operators need to geolocate the source of the jamming to stop it from broadcasting.
AoA geolocation
RFeye arrays can perform angle of arrival (AoA) geolocation of jammers in GNSS-denied environments to determine the location of a signal source based on the angle at which the signal arrives at different sensor locations.
RF sensors inside the RFeye Array determine a line of bearing for the incoming signal by measuring the signal strength across the antennas, allowing the sensor to estimate the direction of the signal. By comparing data from multiple sensors that show the point of intersection, the accurate location of the signal source can be triangulated.
TDoA geolocation
Fixed deployments of RFeye Nodes and Arrays can perform 2D and 3D TDoA geolocation of jammers in a GPS-denied environment with the help of two optional components:
- GNSS Holdover module
- Anti-jam CRPA antennas
The GNSS Holdover module ensures the RFeye Node continues to receive an accurate timing reference even when the internal GNSS receiver is compromised by jamming. It allows operators to continue performing geolocations by providing accurate timing to within 1.5 µs for up to eight hours.
The RFeye Node automatically switches between GNSS and the holdover module depending on the availability of a viable GNSS signal. Using the Holdover module, militaries can then use TDoA geolocation to identify and neutralize the source of the jamming to resume GPS functionality.
However, the Holdover module does require a period of between four to five days to learn the timing reference, so it is a solution for fixed locations, whereas CRPAs can be used for tactical scenarios.
Conclusion
The proliferation of GPS jamming means military and civilian navigators must change tactics. Ceasing operations is not an option, and avoiding heavily jammed areas is costly; therefore, operators need to rely on technological solutions: taking steps to protect GNSS connection, understanding when jamming is occurring, and geolocating the source of the jamming.

White papers & reports
Augmenting border security & defense with Radio Frequency (RF) sensor technology
This white paper was guided by the results of a border security survey aimed at border control, border security, and military personnel tasked with national security and defense. It examines how RF sensor technology can be used to tackle modern border security threats.
Jaimie Brzezinski
Jaimie Brzezinski is Head of Content for CRFS. His specialty is turning highly technical ideas into engaging narratives. He has 15+ years of experience in writing technical content and building global teams of subject matter experts.
