TSCM RFeye Guard
Continuous real-time in-building monitoring for Technical Surveillance Countermeasures


RFeye Guard overview
RFeye Guard is a sophisticated in-place spectrum monitoring and threat geolocation system for 24/7/365 TSCM. It combines highly sensitive and broad bandwidth receivers with real-time and autonomous software to ensure you never miss an illicit signal.
This high-specification technology offers continuous spectrum monitoring up to 40 GHz and is designed to detect signals that are likely to be missed by handheld sweepers. Its high sweep rates of almost 400 GHz/s and resolution down to 1 Hz make it a robust system designed to provide a 100% probability of intercept (POI) for unauthorized transmissions in real-time.

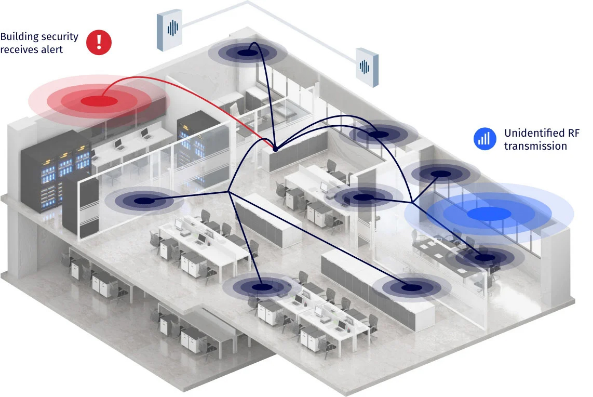
RFeye Guard relies on a network of permanent RF receivers discreetly installed in ceiling kits. They continuously scan and sweep the electromagnetic spectrum for unauthorized transmissions. When they detect an illicit signal, RFeye software calculates its exact location using Power on Arrival (PoA) and issues security with an alert.
- Real-time and automated 24/7/365 surveillance
- Complete RF security
- Integrates with existing building aesthetics
- In-building geolocation of bugs and exterior monitoring
- SyncLinc technology for accurate geolocation
RFeye Guard at a glance
Intelligent RF sensor
Timing synchronization
indoors
Networked for multiple
users & missions
Superior RF performance
100 MHz IBW wideband frequency monitoring

Easy installation,
setup & operation

BROCHURE
Continuous real-time in-building monitoring for Technical Surveillance Counter Measures
In an era where the threat of espionage is a real-world concern, protecting sensitive information and ensuring your facility’s security is paramount. RFeye Guard offers continuous, real-time in-building monitoring designed to combat the ever-growing threat of covert surveillance devices.
RFeye Guard - Detect. Locate. Protect.
RFeye Guard helps protect critical infrastructure, government entities, and corporations from the increasing threat of state and corporate espionage.
RF transmitters used for espionage are discrete, capable, and accessible—from $20 bugs available online to highly sophisticated RF covert listening devices hidden inside USB cables, light bulbs, or authorized electronic devices. These devices are very difficult to locate and can lie dormant until connected to a mobile network.
Vigilant entities focused on robust operational security will want to invest in multi-layered Technical Surveillance Countermeasures to detect and address any threats. This approach combines physical security, bug sweeping, and an in-place monitoring system for round-the-clock monitoring and immediate detection of security breaches.

ENSURING RF SPECTRUM SECURITY AT A HIGHLY SECURE FACILITY
How a security service detects and geolocates unwanted signals to safeguard national security
Read the storyKey questions
When choosing a TSCM solution
for your facility you should
consider the following

- What is the type and size of your facility where the system will be installed?
- What specific frequency ranges and types of signals need to be detected?
- How will the system integrate with your current security or surveillance systems?
- What level of technical expertise is available for operating and maintaining the system?
- Does the system’s modularity and software customization meet specific needs and allow for future scalability?
- What training is required for staff to operate the system effectively?
- What level of customer support and technical assistance do you need post-installation?
Talk to an advisor about the RFeye Guard
Get instant news & expert insights
Join thousands of professionals who subscribe for exclusive insights and early access to our reports and analysis.
Related reading


